Most people understand it as the technology underpinning Bitcoin. However, Blockchain’s potential use cases spread far beyond cryptocurrencies. In fact, it has been touted as the next generation of the Internet, also called Decentralised Web or Web 3.0.
Blockchain Explained for Dummies
(Blockchain technology explained simply)
So what exactly is Blockchain?
In this article, we delve deeper to provide you with an in-depth overview of this technology that is already revolutionising how the world works.
Blockchain explained in 10 words
Blockchain is a kind of distributed ledger comprising of unchangeable records.
Blockchain explained in 100 words
Since ancient times, ledgers have played an important role in commerce, often recording many things, most ofthe common ones being assets such as money and property. In the past, ledgers used to be recorded on clay tablets, papyrus, and paper. They later transitioned to bytes as computerisation gained momentum.
As a distributed ledger, Blockchain is effectively an electronic asset database which can be shared across a network of multiple computers (called nodes) spanning multiple locations, institutions, or geographies. All the nodes have their own copy of the database,and any alterations to theledger are mirrored in all the other ledgers within minutes, or some instances, seconds.
The accuracy and security of the assets stored in the databaseare maintainedvia cryptography involving keys and signatures that controls which node can do what within the ledger.
Blockchain explained in 1000 words
Blockchain relies on cryptography as a way of protecting the identities of nodes, ensuring that transactions are conducted in a safe, transparent and immutable manner. Thus, any person using Blockchain can have confidence that once a transaction has been recorded on the Blockchain, it is legitimate and cannot be forged.
Despite originating from cryptography, Blockchain relies on crucial asymmetric cryptography (sometimes called public-key cryptography), which is better suited to the functions associated with it than its symmetric-key counterpart.
Symmetric-key verses public-key cryptography
To understand Blockchain better, let us see how symmetric-key and public-key cryptography works.
Suppose Alice wants to share her items with Bob. If she has a box containing a lock, then the lock typically has a key for locking and unlocking the box. If Alice wishes to protect his belongings, sheplaces them in the box and locks it. Since she wants to share his items with Bob, she can duplicate his key share and share it with Bob.
This is how symmetric-key cryptography works:
You have one key that you use it to encrypt (or lock) the data to generate a ciphertext and decrypt (or unlock) the ciphertext to generate the original message (or plain text) as shown below:
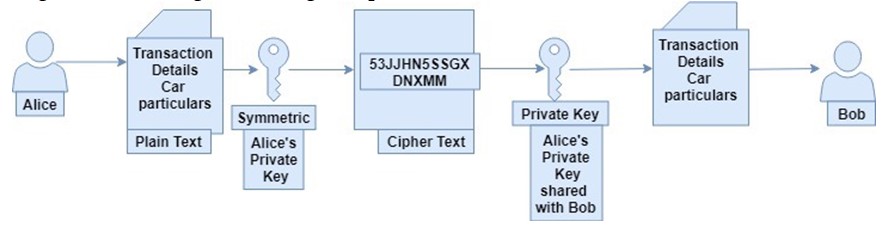
Symmetric-key is considered less secure because the key can be accessed by a third-party thereby compromising communication between Bob and Alice.
What about public-key cryptography?
Alice has a box, but this time the box has a special lock. Rather than having just two states as was the case with symmetric-key, Alice’s box has three states(locked, unlocked and locked). The box also has two separate keys:
- Locking key (which can only turn clockwise from lock-unlock-lock states); and
- Unlockingkey (which can only counterclockwise(from lock to unlock to lock).
In this case, Alicepicks the first key and keeps it to herself. In cryptographic terms, this key becomes her “private” key because no one else can have it while the second key becomes her public key. In fact,she can make thousands of its copies and distribute to his friends (Alice included).
Now, suppose Alice wants to send Bob a personal item.
Naturally, Alice places the item in the box and lock the box using use Bob’s public key. Because Bob’s public key can only turn counter-clockwise, it locks the box, and once locked, no key apart from Bob’s can unlock it. This means that even Alice cannot unlock Bob’s box and get her item back after packing.
This is an example of public-key cryptography. Thediagram belowillustrates the concept further:
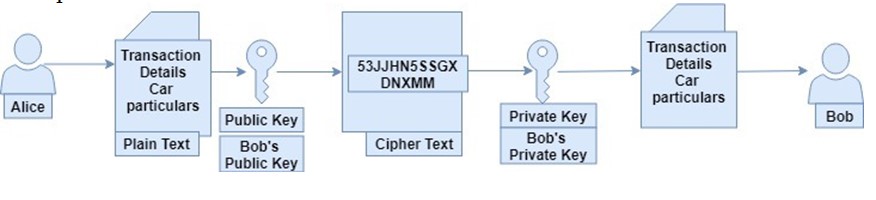
Blockchain uses the same concept of public-key cryptography.
Suppose Alice wants to sell her car to Bob.
First Alice must generate her keys (both private and public) that she uses to identify herself and confirm the car transactions to Bob. Whereasher public key is made available to the whole world, her private key remains safe and secret. Obviously, the 2 keys generated must correlate.
Also, keys must be produced in a manner where all users can verify Alice’s public key, but no one (even Bob) can reverse her private key if he/she knows the public key. For the transaction to be confirmed on the Blockchain, Alice signs the transaction using her private key to produce a digital signature.
Alice’s digital signature helps the network to authenticate Alice’s identity to Bob. To generate a digital signature, Aliceuses her private key and the transaction information (particulars of the car) she is selling to Bob to create a hash value which is stored on Blockchain. A hash value, which is created by function, is a fixed-size string that is broadcasted to the entire network.
Often, a digital signaturehas two essential functions:
- Sign (Transactions, Private Key): This function picks Alice’s private key and transactions to create a signature
- Verify (Message, Public Key, and Signature): This function verifies the identity of Alice using the broadcasted message, Alice’s public key and signature.
Put simply; given the transaction details and a private key, a hash function usually creates a unique digital signature for that transaction, given the message to verify, public key, and signature, a hash function always generates the identity of the sender based on whether the signature is valid or not.
When Alice signs off her transaction, it is sent to the network where it awaits to be confirmed by other nodes (often called miners). Miners use Alice’s public key (since they already know it) and the broadcasted hash value to ensure the signature is valid in a consensus algorithm.
Essentially, all the nodes in the network must agree that the signature is valid for it to be added to a block. If the signature and ownership check out, a transaction is immutably (permanently) recorded in the block. All confirmed and authenticatedtransactionsare placed on blocks that are linked and chained together the start of the chain (often called the genesis block) to the most recent block, and thus the name Blockchain.
Here is a summarised diagram explaining how Blockchain works:
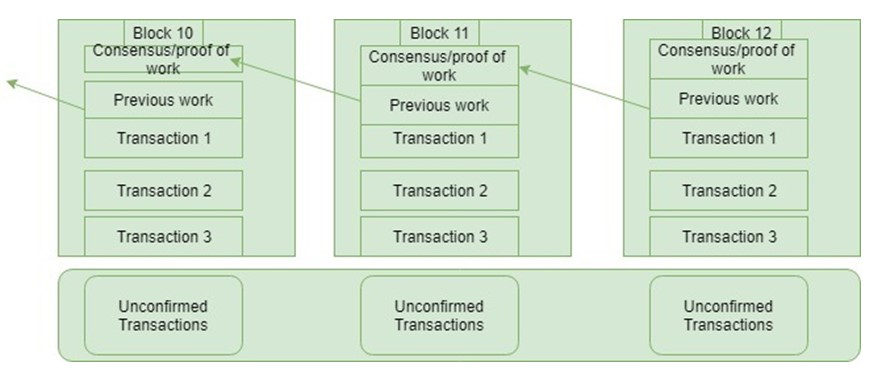
Due to cryptographically-generated digital signatures and consensus algorithms, Blockchain provides an auditable history of the transactions without the involvement of centralised or third parties.
Putting it all together
Blockchain is slowly ushering in a resilient and next-generation internet for both registry and exchange of tangible and intangible assets. You can be part of this silent revolution if you understand what it entails. We would be glad to help your organisation leverage Blockchain for both social, economic, and political activities.